How Can Drones Be Hacked? Complete Guide

It’s 2019, and we live in an age of hackers. Drones are here, they are more popular then ever and today almost every child wants it. But are the drones protected, can they be hacked at all, and if so how? So Can Drones be Hacked? The answer is „YES“. They can, and have been hacked. There are several ways drone can be hacked and some of them are simple while some are complicated. When we talk about hacking a drone, this is not just a theory and there were already cases where the high-powered unmanned aerial vehicles (UAVs) increasingly employed by military forces were hacked.
One of the most famous examples of what happened to drone hacking is the one from 2011 when the Iranian military took control of the American UAV. They were able to do this by finding the frequency at which that drone was, and they used GPS navigation to bring it down. So when we talk about commercial drones, what programming language should you start out if you want to Hack a Drone? It does not matter, because all modern programming languages are wildly powerful and they can do all kinds of things.
Drone Vulnerability
Latest research shows drones are vulnerable to cyber attacks, and it’s not just individuals who are at risk. Corporations are incresingly using drones to AID their operations. Critical infrastructure, the police and military, agriculture facilities, the construction sector, your drone’s photos and films can be stolen. The attacker for example logs in to the DJI FlightHub with a stolen user ID token. The token is then switched with the attacker’s own ID to gain access to the drone’s camera, and see exactly what you see. Another attack option is to gain access to your drone’s flight data stored in the cloud. Your sensitive data is not as safe as you think.
One of the most popular and the top-selling drones on Amazon is vulnerable to hacking, and many more are at risk. And similar models from other supplieres appear to be impacted by the same vulnerability. Researchers at UT-Dallas just hacked into the DBPOWER Quadcopter. It’s one of the most popular drones on Amazon and is originally priced at $140. The quadcopter boasts an HD camera with VR headset capability. But the drone’s security can easily be compromised. This vulnerability means a malicious hacker can easily kill your drone mid-flight. But making it crash isn’t the worst thing that can happen. When a drone gets hacked, the hacker can download private photos and videos, without the victim even
Popular Software Programs for Hacking Drones
Maldrone aka Malware for Drones: the malware which hijacks your personal drone. When we talk about Maldrone, this is a type of malware specifically aimed at UAVs and via Internet connections you can hack into drones. We need to consider that drones are essentially flying computers, and so they are susceptible to the same type of hacks as a laptop or smartphone. According to the researcher, Maldrone can be used to remotely hijack drones via entry through the backdoor and one of them is Linux system. With that you can easily take over the malicious code is able to kill a drone’s autopilot and take control remotely.But the malware isn’t the only problem related to the increased use of UAVs, there are others.
SkyJack aka Zombie Drone Software: lets you hunt down and hack other drones from the air. So how, exactly, does SkyJack work? It is a drone software that runs with your drone and actually uses a Raspberry Pi computer, flies around and looking for other drones. As soon as it finds any other drones, it hacks into that drones wireless network, disconnects the owner and then takes over that drone, creating an army of zombie drones under your control. SkyJack is application which runs off of a Linux machine.
How Hacking Drone Process Work?
GPS Hacking. With this way we will explain how this whole system works and how it is possible to hack even the most secure UAVs in the world.
• GPS Signals (Military v/s Civilian)
Civil GPS systems differ in how they are not encrypted and can be accessed much more easily. The civilian GPS system allows signal propagation by means of special codes. But military GPS Is not necessarily more accurate unlike the civilian. The user range error of the GPS signals in space is actually the same for the civilian and military GPS services. Civilian devices are based on only one GPS frequency, unlike military devices that use at least two GPS frequencies.
• How Exactly GPS Signals are Received?
From a satellite the timing pulse was sent to create a certain distance from the satellite. We can see from the picture that each of these satellites is quite far from the given receiver, but its circles intersect at some point. When we look 2 spheres that are representing 2 satellites, they are intersecting and make a circle. 2 intersceting spheres together with the Earth make 3 circles that give an actual position in 3D space.
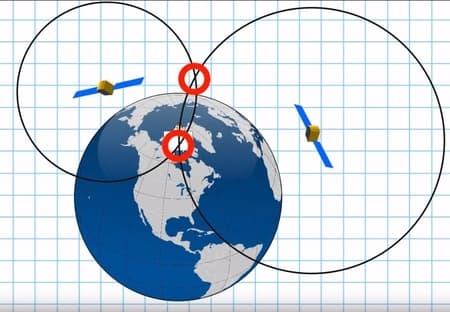
• GPS Spoofing Scenario
The definition of spoofing attack is when a person or program try and manage to successfully masquerades and falsifying data to gain an advantage. A GPS spoofing attack attempts to deceive a GPS receiver by broadcasting incorrect GPS signals, structured to resemble a set of normal GPSsignals, or by rebroadcasting genuine signals captured elsewhere or at a different time. What the hacker will do is replace the real controller with the fake with spoofing option.

• Attack Method – Replay attack
This method is actually displaying the identical authentic signal and sending that signal with a certain delay. This method works by using a “time of flight” signal to simulate and give a false image that it is actually more distant than it is. This method is used to require the use of multiple real-time satellites in conjunction with a transmitter, thereby overriding signals coming directly from the satellite.
• Software for Hacking GPS: BladeRF
This is a USB 3.0 Software Defined Radio. The 40KLE option makes the bladeRF the essential low-cost RF transceiver kit for both hobbyists, and RF enthusiasts. the bladeRF has Frequency range between 300 MHz – 3.8 GHz without the need for extra boards.

Anti-hacking Solutions
What was consider the biggest challenge is to encrypt the civilian GPS. And there was the digital signatures that have been exchanged between Receiver and Satellite. You can also take care of the hackers with a good anti hacking app. The point of all this is to secure the way of data is to encrypt them, by that we have safely protected the individual’s privacy and the data itself. Never reuse a password that was stolen, or use any altered version of it because your CNetID account and your personal information will remain at risk. No one offers a more comprehensive portfolio of Assurance, Testing, Inspection and Certification services to ensure drone quality and safety, so you need to test your product.
Military “Predator” Hacked With $26 Software
Militants in Iraq hacked U.S. Predator drone using off-the-shelf software to download and watch military surveillance video. The famous Predator, the US special equipment that they used in Iraq and Pakistan have been hacked by insurgents using the software that is available online for only $26. The terrorists used software programmes which were available on the internet and were not hidden at all, and one of them was Skygrabber, which was exclusively for downloading music. The program works by collecting a Drone signal that goes all the way to the Regional Ground Station, and then via Commercial Satellite, before it goes and downloaded by U.S. Control Center and that is the last point that is vulnerable. The Pentagon knew for this problem but their assumption was that they didn’t any knowledge to intercept these potential feeds. What they did was they were able to intercept the frequency of the drones, thereby transferring everything to the controller and thus discovering their potential targets.
Conclusion
We’ve got a pretty clear and detailed answer to this question: „Can Drone Be Hacked?“ and the answer is Yes!. After all this, we can conclude that drones are vulnerable, and much remains to be done to secure them. Most popular softwares that people use now for hacking drone are Maldrone and SkyJack, but there are also a lot other programs. I also explained that drone’s GPS receiver is one of the biggest weaknesses in today’s drones. What we have concluded is that we need to use strong encryption, alter passphrases and to test our product. I hope this helped you and you will know how to apply it!

