Can Drones Be Hacked? Ways, Tips, History
There are more and more drones (quadrocopters) in the sky, and they are gradually “getting smarter”, and becoming more functional. Drones of this types are not only entertainment, but they help athletes, photographers, scientists and, of course, attackers of all kinds. With the help of drones, unauthorized surveillance of people, industrial and other objects is often carried out. There are companies that began to create protective equipment against drones, allowing you to land the device or seize control over it. We can say that drone manufacturers are also trying to protect their devices from interception. However, this is not so easy, especially if the actual experts in their field address the issue.
So Can Drones Be Hacked? Yes, drones can be hacked very easily today, which means the „attacker“ can take control of your drone within a few seconds. Some of the methods that can be used to hack a drone are: GPS-spoofing, vulnerability of a mobile applications, by WiFi transmitter, by electron guns and so on.
Is it Hard to Hack a Drone? Proven Methods
In the market appeared information that the research team has created a system that allows you to seize control of almost any drone. Moreover, this does not require an electromagnetic gun, the permission of the authorities or something else. It is enough to use a specially modified control panel. Specifically, this type of hack allows you to take control of drone with any communications protocol DSMX . This protocol is used not only for data exchange with drone, but it is also used for working with radio-controlled cars, boats, helicopters, etc.
This method proposed by experts, allows you not only to intercept control, but also to form a “digital fingerprint”, unique for each device. This fingerprint can be used to distinguish “one’s” device from “another’s” and form a list of trusted systems. The technology does not involve the use of a jammer that blocks communication between the drone and the control device. Instead, a complete control interception is practiced while maintaining the functionality of another’s drone.
This method is not something new. It has been used by some cybercriminals and information security experts for a relatively long time, without making the method widely known. At the conference, this method was first discussed, providing an almost complete technical description. So, to intercept control over an alien drone, Anderssen uses a time attack (timing attack), synchronizing the frequency of the transmitter emitter with the frequency of the drone’s radio module in automatic mode. After that, a malicious packet is sent to the drone, which forces the alien device to ignore commands from the “native” controller and start listening to commands from the attacker’s controller.
Drone Hacking Using Attacker’s Controller
It is clear that now devices such as what Andersson demonstrated are not well known to the general public. But a radio technician can easily create such a device, knowing the features of the communication protocol between the drone and the controller. Perhaps after this demonstration there will be companies and individual craftsmen who will sell controllers for intercepting other people’s drones. According to experts, there is nothing particularly complicated about this. The vulnerability that opens the ability to control other people’s devices is contained in the systems of almost all radio-controlled devices that support the DSMx protocol.
Of course, this method can be used not only by attackers. Law enforcers, noticing a violation by a radio-controlled device, can also use this method to intercept an intruder. The owners of any property (houses, land, etc.) can do the same, taking control of a drone or drones that invade other people’s property. According to Andersson, it is impossible to solve the situation with interception of drones right now – this vulnerability is relevant for many models of radio-controlled devices. Their manufacturers will not be able to quickly change the protocol or type of radio-controlled module that is installed in the device. The solution may be the release of such modules, the firmware of which can be updated. But it is both expensive and long.
Experts also argue that the time attack demonstrated by Anderssen affects all modern radio-controlled systems. To carry out such an attack, you need a little knowledge about the device of radio-controlled devices and protocols that are used to transmit data over a wireless network, as well as electronic components worth about $ 100. The most interesting thing is that the second attacker can use a similar system to crack the first, which, in turn, took control of someone else’s drone.
Another type of hack is used, based on the vulnerability of Xbee chips. They are installed in a large number of different models of radio-controlled devices. Chip data encryption is supported, but in many cases, developers disable it. That is why an attacker can crack a drone with such a chip from a distance of several kilometers. The only way to protect, according to the author of this method of hacking, is to use data encryption.
Using Electron Guns to Hack Drones
A simpler way of influencing the drone is an electron gun. Batelle has already created several such devices. The most effective can be called a gun DroneDefender. With its help, you can create a radio silence zone around the drone. The gun generates a powerful radio signal that interrupts the signal from the drone. In addition, GPS or GLONASS positioning is also violated.

In 2016, the few company introduced the “radio gun”, which also creates powerful interference across the entire radio spectrum around the drone. The difference between the gun and DroneDefender is the ability to determine the type of signal transmitted by the drone, creating interference only for the used radio frequency. A gun can even transmit commands, including “home” and “land.” Teams are suitable for a large number of drone models. Perhaps the most unusual way to neutralize a drone is to “hunt” a drone using another drone and a network. A “cop” drone carries a network that is thrown at an intruder drone. In case of a successful maneuver, the intruder can be neutralized.
Drone Takeover Completed in 11 milliseconds
A researcher specializing in computer security has developed a box capable of intercepting the connection between a drone and its radio remote control to allow control of it in flight. Now drones are used in various situations, but security experts have revealed drone vulnerabilities. In just 11 milliseconds, an expensive drone can be hijacked. Recently drones are used everywhere. Amazon uses a drone to deliver items. Filmmakers and the media flew the camera over the sky to shoot an attractive bird’s-eye view. Cyber enthusiasts who are willing to pay more than $500 for smart toys enjoy sky exploration and aerial photography. But what if for some reason the controller stops functioning in the middle of the air?
It is not a firmware bug, nor is it a controller failure. The drone was hijacked. Security expert Jonathan Andersson proved at the Security Analyst Summit that a skilled person can create a device that can take over a drone in a matter of seconds. He created takeover devices using software-defined radio (SDR), drone controllers, microcomputers, and other electronic devices. This device was named Icarus. Mr. Anderson used SDR to find the signal transmission method through trial and error according to the communication frequency between the drone and the controller.
After all, the frequency changes one after another every 11 milliseconds. Once you are successful, the path to take over the drone is clear. All smart toy developers use a similar protocol. As a result, the drone’s legitimate controller can no longer be used, and the hijacker controller takes control in no time. This threat can affect the entire drone industry, from cheap toys to expensive and professional drones. This is because drones and controllers use data transfer protocols that are vulnerable to similar attacks. This is a problem that can be solved by changing to strong cryptography, but since many controllers do not support software updates, it will be difficult in practice. In addition, strong cryptography requires significant computing power, which increases controller and drone power consumption.
Icarus, the case where you can hack any drone in full flight
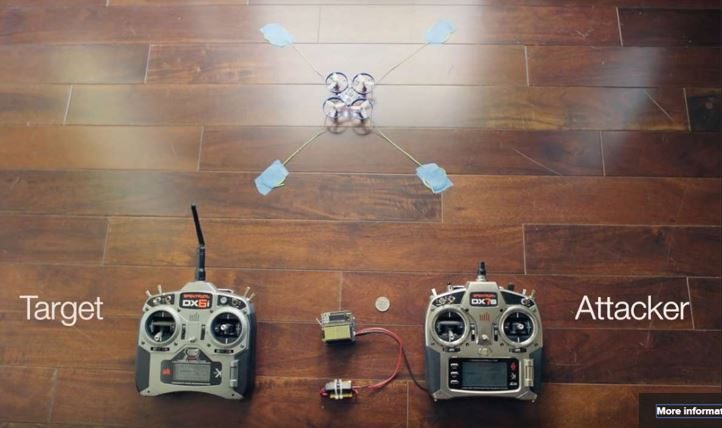
Many Drones Use the DSMx Protocol
Icarus exploits a second flaw through which data packets for the takeover take precedence over those of the original remote control. As can be seen in this demonstration video posted on YouTube , once the hijacking is operational, only the remote control associated with the hacking box is active. In addition, the operation can be performed while the aircraft is in full flight.
Many technical solutions are being studied in order to put a drone out of service without reaching such extremes. It can include using a jammer (or jammer ) or sending another drone with a net to capture it. In the Netherlands, police have even successfully tested the use of an eagle to capture drones. The Icarus solution has the advantage of being able to control the machine without the risk of damaging it or injuring someone by causing a crash. The downside, this device could also make the happiness of malicious people.
What is a Drone Jack?
When a plane is hijacked by a terrorist group, you don’t know where to go and what dangers will occur. Also, when a computer is taken over by a cyber attack, it shows various behaviors that have nothing to do with your will. Recently, drones (UAVs) that fly over the air are rapidly spreading and are not only enjoyed as a hobby but also used in various places such as delivery and media photography. But what happens if a drone is taken over? Let’s take a look at this “Drone Jack“.
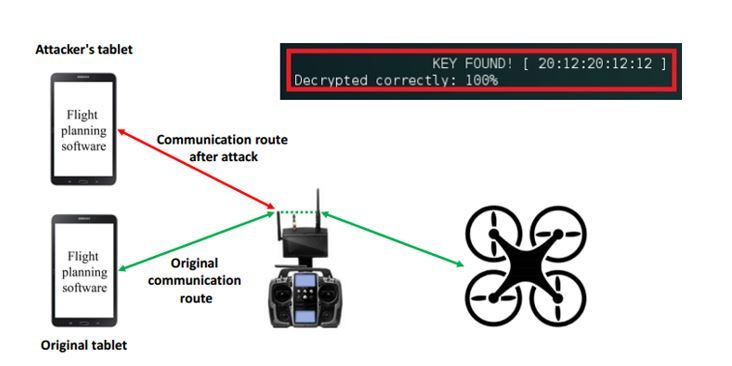
„Drone Jack“ is a phenomenon where the drone you are operating suddenly becomes uncontrollable by yourself, whether it is a hobby or work, and you are taken over by someone else’s control. How does the drone jack, which exploits cyber attacks including unauthorized access, work? To explain in simple terms, drone jacks are performed as follows. Decrypt communication between drone and controller. Send a fake command to a drone on a computer with a transmitter. In many drones, it is said that there are many cases where communication with the controller is not encrypted or only a mechanism that can easily break through is implemented. In such a state, it is said that it is relatively easy to try unauthorized access.
Drone Jack Attack Case
Venezuela (August 2018)
The first is a case in Venezuela that occurred in 2018. This is that the country’s President Maduro was about to be assassinated by a drone carrying explosives during a ceremony in the capital. In this case, it is said that two drones were used.
Japan (April 2015)
In Japan, an example of 2015 was a drone falling on the roof of the prime minister’s official residence. Although it has been reported that the aircraft was marked with radiation marks and smoke cylinders, it was not particularly dangerous.
Police Drone Hacked With $40 Equipment
The researchers discovered two vulnerabilities that made hijacking of drones even possible. Firstly, very weak encryption is used for Wi-Fi communication between the drone control module and the operator’s device: it has long been known that WEP can be opened in seconds. This weakness can be exploited at a distance of 100 meters from the drone. That is, the attacker can infiltrate the connection between the drone and its operator, send a malicious command to the UAV and simply disconnect it from the home network.
Secondly, the Xbee chip, which is used by many UAV models, is unsafe. Although Xbee supports encryption, due to performance issues, so that there are no delays between the operator’s commands and the drone’s response, it’s completely disabled. Thanks to this, an attacker can carry out a man-in-the-middle attack, being at a distance of two kilometers from the drone.
“An attacker can redirect packets, block the [real] operator, or simply pass all packets through himself, but I think most attackers would simply steal a drone,” the researcher said.
You can protect yourself from hijacking or hacking a drone, according to Roddy. To do this, it is enough to make sure that all communications between the aircraft and the operator’s application are securely encrypted.
Hisotry of Hacking Drone Incidents
It is very strange that at hacker conferences there were one and a half speeches on hacking drones.
I fussed around and made a selection of all available hacking cases. Both military and civilian.
Some facts:
- Today, more than 70 countries produce unmanned aerial vehicles (drones) for the needs of the army, police, the Ministry of Emergencies, etc.
- 127,000 drones soldon eBay from March 2014 to February 2015
- The warrior now has about 20,000 drones
- 10 real and 2 invented cases of drone hacking.
2009
Location: Iraq, Afghanistan
Model: Predator unmanned aircraft (US $ 4.03 million, 2010)
Burglar: Iraqi hackers
Vulnerability: data transmission channel from UAVs to the receiver
First time the US military in Iraq faced video capture in 2008, when a rebel was taken prisoner, on whose laptop were stored images obtained from American drones. In the summer of 2009, computers were also discovered with several hours of video recordings from UAVs.
According to the newspaper, citing data from senior military officials and intelligence officials, the rebels used unprotected communication channels with UAVs for video capture. At the same time, they used software such as, for example, SkyGrabber, which can be bought over the Internet for only $ 25.95. SkyGrabber, according to the description of the Russian manufacturer SkySoftware, “receives and processes the traffic transmitted from the satellite, extracts files from it and saves them to your hard disk in accordance with the configured filters.”
2011
Location: Iran
Model: RQ-170 Sentinel
Cracker: Persian specialists
Vulnerability: GPS-spoofing
Iran presented to the media a press release that spoke about the successful interception of an American unmanned aerial vehicle such as the RQ-170 Sentinel. Among other versions of the interception of the device, there was one that related to the use of special electronics, which drowned out the GPS satellite signal and replaced it with its own. As a result of these actions, the drone automatically, guided by the global navigation system, began to return home. Since the true signal of the satellites was drowned out by a false one, the RQ-170 sat on the Iranian airfield, taking it for its “native” one. However, this is only a version, although quite plausible. The first reports of this method of interception came soon after the publication of the press release and they were made with reference to a certain Iranian engineer, Iranians are constantly trolling Americans. First, they wanted to massively sell toy RQ-170 Sentinel at a scale of 1:80, and in 2014 they saw a full-size copy of an article on Habr with a discussion of the possibility of hacking the GPS system RQ-170
2012
Location: Moscow, PHD
Model: AR.Drone
Burglar: Sergey Azovskov aka LAST_G
Vulnerability: vulnerability of a mobile application
According to the competition, the organizers launched a miniature aircraft controlled from a smartphone via a Wi-Fi network. Participants were invited to connect to the drone using their own programming knowledge, to deprive the organizers of the ability to control the device and switch control to their smartphone. According to Azovskov, the process of depriving the organizers of the rights to control the drone did not cause serious difficulties.
Related Article: How To Secure Your Drone From Hackers? 5 Best Way
2013
Model: AR.Drone
Burglar: Samy Kamkar
Method: Aircrack-ng , Raspberry Pi installed on the drone, WiFi transmitter and receiver:
Kamkar said that he used the Aircrack-ng utility to break into a wireless network, and quadrocopters the network was able to detect due to the features of their MAC address. All quadrocopters of this type have the same type of address, which makes it possible to distinguish them from other wireless devices. SkyJack monitors the MAC addresses of Wi-Fi networks in the signal coverage area, and then blocks them using its drone and disconnects the device from which it was controlled from the iOS or Android device. After that, the hacker can control the direction, speed and altitude of the drone, as well as receive images from cameras.
2014
Location: United States
Drones: Parrot AR.Drone and DJI Phantom
Hackers: Hack5 YouTube Channel Leaders
Method: WiFi Pineapple
WiFi Pineapple is a product of enterprising Americans who ordered a Wi-Fi router with two wireless interfaces and one wired from the Chinese, wrote firmware for it based on OpenWRT and stuffed it with utilities for hacking / intercepting and analyzing traffic. The presenters fastened the WiFi Pineapple to the DJI Phantom and then chased the AR.Drone and knocked it out.
2015
Cracker: Rahul Sasi
Target: Parrot AR.Drone 2.0 and DJI Phantom
Vulnerability: ARM Linux
Sashi applied reverse engineering to the proprietary AR Drone program.elf Researcher claims that a “combined” attack using Maldrone and Skyjack will allow to intercept multiple targets and thus create a whole squadron of zombie drones. Given the growing interest in civilian UAVs from corporations such as DHL and Amazon, the picture is truly sinister. In addition, using Maldrone, an attacker can not only hijack the drones themselves, but also spy through the built-in cameras, intercepting video traffic from the attacked devices.
“After my malware attacks the controllers, the engines stop and the drone starts to fall down with a brick,” the researcher explains. “However, the backdoor instantly takes control, and if the height is really big, there is enough time to avoid a fall.”
Conclusion
As we can see drone hacking is not a problem for today technology. There are devices that can take control of a drone in just a few seconds. Therefore, there is still plenty of space to work on to make drones safer. I also described some of the most important historical events where drones were hacked and used for malicious purposes. If you would like to comment on this topic or add something of your own, feel free to leave a comment below.

